What is Attack Surface Management?
Your organization’s attack surface is constantly evolving. New assets, cloud services, and shadow IT can leave you exposed—often without your security team’s knowledge. If you don’t know what you have, you can’t protect it. NCC Group’s Attack Surface Management enables your organization to gain complete visibility and control over digital assets, so you can defend what matters most.
ASM is the continuous process of identifying, monitoring, prioritizing, and securing all digital assets—internal and external, known and unknown—that could be targeted by attackers.
By looking at your organization’s entry points through the eyes of a hacker, you can proactively address exposures and reduce your business risk.
Why does ASM matter now?
1 in 3 data breaches involve shadow IT
If you don’t have a clear inventory of your assets, you can’t be confident they’re protected.
The cyber skills shortage persists
Security teams are stretched thin. Our managed service frees up your team to focus on what matters—mitigation and risk reduction.
Attackers only need to find one weakness
Don’t leave your “windows open” while locking the doors.
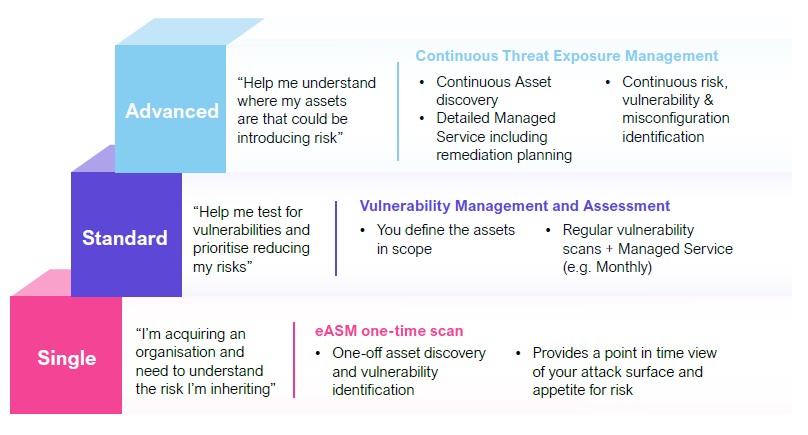
Our proactive, continuous, and integrated approach
NCC Group’s ASM service is built on a three-tiered model to fit your needs and maturity level.
Already invested in ASM technology? We can wrap our managed service around your existing tools, maximizing your investment and providing expert guidance.
Reduce your overall business risk
Our ASM solution distributes your assets into their specific subsidiary, streamlining the process of getting the right information to the right security team quickly with the relevant business context. Depending on the service tier purchased, NCC Group can ingest data from other vulnerability management tooling to correlate and prioritize it alongside your risk appetite.
Key features and benefits:
Asset discovery
across your internal and/or external assets.
Comprehensive identification
for risks, vulnerabilities, and misconfigurations combined with exploit and threat intelligence
Cross-capability coverage
that feeds into other security programs for a unified view.
Risk prioritization
aligned to business risk appetite, and with integrated reporting and remediation guidance.
Rapid breach response
Know exactly where assets are located and who's responsible to enable faster containment.
Secure your digital landscape today.
Talk to one of our experts to revolutionize your cyber security strategy.